Placing a firewall in a corporate network puts you in commanding position to protect your organisation’s interest from intruder. Firewall also helps you to publish contents or share infrastructure or share data securely with eternal entity such as roaming client, business partners and suppliers. Simply, you can share internal contents without compromise security. For example, publishing Exchange Client Access Server, OCS 2007 and SharePoint front-end server in the perimeter.
More elaborately, the front-end and the back-end topology is commonly seen in multi-tier applications where the user interacts with a front-end server (Example: CAS server) and that server interacts with a back-end Server (Example: HT server). In this exchange deployment scenario, users interact with a front-end CAS Web server placed in DMZ or perimeter to get Outlook Web Access for reading and sending email. That Web server must interact with the back-end mail server or HT server, but Internet users do not need to interact directly with the back-End HT server. The front-end and back-end server(s) does all these for you providing maximum security. visit Exchange 2010 deployment in different firewall scenario
In this article, I am going to illustrate Back-to-Back Firewall with DMZ. This topology adds content publishing to the back-to-back perimeter topology. By adding content publishing, sites and content that are developed inside the corporate network can be published to the server farm that is located in the perimeter network.The following illustration shows the back-to-back perimeter topology with content publishing.
Advantages
- Isolates customer-facing and partner-facing content to a separate perimeter network.
- Content publishing can be automated.
- If content in the perimeter network is compromised or corrupted as a result of Internet access, the integrity of the content in the corporate network is retained.
Disadvantages
- Requires more hardware to maintain two separate farms.
- Data overhead is greater. Content is maintained and coordinated in two different farms and networks.
- Changes to content in the perimeter network are not reflected in the corporate network. Consequently, content publishing to the perimeter domain is not a workable choice for extranet sites that are collaborative.
Assumptions:
- Internal IP range: 10.10.10.0/24
- Perimeter IP Range: 192.168.100.0/24
- Public IP:203.17.x.x/24
Note: In the production environment, perimeter IP must be public IP accessible from internet.
| Computer | Internal NIC Configuration | External NIC Configuration |
| Back-End TMG 2010 (two NICs) |
IP: 10.10.10.2 Mask:255.255.255.0 DG:Null DNS:10.10.10.5 |
IP:192.168.100.4 Mask:255.255.255.0 DG:192.168.100.5 DNS:Null |
| Front-End TMG 2010 (Two NICs) |
IP:192.168.100.5 Mask:255.255.255.0 DG:null DNS:10.10.10.5 2nd DNS:203.17.x.x (public IP) |
IP:203.17.x.x (public IP) Mask:255.255.255.0 DG:203.17.x.1 (public DG) DNS:203.17.x.x (public DNS) |
| DC | IP:10.10.10.5 Mask:255.255.255.0 DG:10.10.10.2 DNS:10.10.10.5 |
Not Applicable |
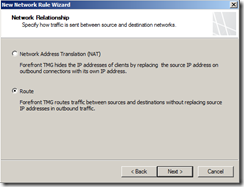
Routing Relation:
| Back-end TMG | Internal to Perimeter Perimeter to External
Perimeter to Internal |
Route NAT (Default)
Route |
| Front-End TMG | Internal to External (All TMG Default) |
NAT (Default) |
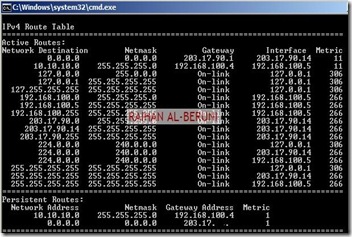
Persistent Routing in Front-End TMG and all servers placed in perimeter/DMZ: You must add following routing table in front-end TMG server and all other servers placed in perimeter in elevated command prompt. To do that, just log on as administrator, open command prompt and type following and hit enter.
Route ADD –P 10.10.10.0 MASK 255.255.255.0 192.168.100.4
Configure Back-End TMG Server:
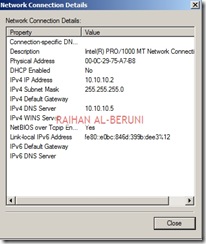
Log on to TMG Server using Administrative credentials and define internal IP as shown on TCP/IP property.
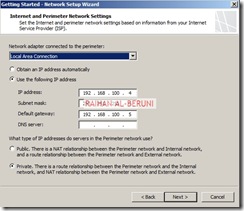
Define Perimeter IP As shown on TCP/IP property
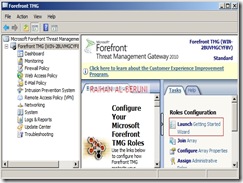
Now add TMG serve
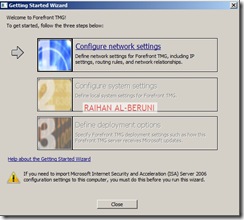
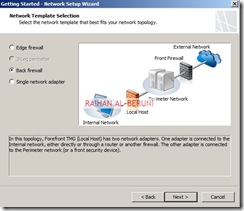
r as a domain member. Install Forefront TMG using Step by Step Guide Lines. Open TMG Management console, Launch Getting started Wizard. Configure network Settings. Select back Firewall.
Click Configure Systems Settings.
Click Define Deployment Options.
Click Close. Apply Changes and Click Ok.
Create connectivity with AD and DNS.
Add and Verify IP addresses of internal (10.10.10.0/24) and perimeter network (192.168.100.0/24).
Add Network Rules:
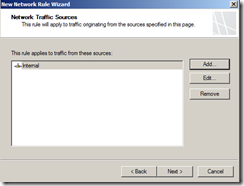
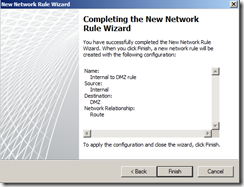
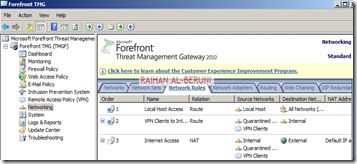
Create Network Rule. To do that click on Networking>Network Rules>Create a New Network Rule Wizard.
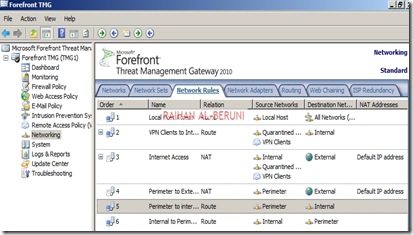
Here, Rules 1 to 4 will created by default while initial configuration as shown below. You have to create rule 5 and 6 by repeating above steps.
Configure Firewall Rules:
| Actions | Allow |
| Protocols | DNS, Kerberos-Sec(TCP), Kerberos-Sec (UDP),Kerberos-Admin (UDP), LDAP, LDAP (UDP), LDAP (Global catalog), Microsoft CIFS (TCP) ,Microsoft CIFS (UDP), NTP (UDP), PING, RPC (All Interface) |
| Source | DC, Front-End TMG |
| Destination | DC, Front-End TMG |
| Conditions | All Users |
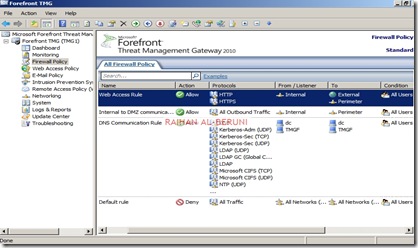
Now Publish DNS for perimeter network. Right Click on Firewall Policy, Click New, Click Access Policy, Name new access policy. On the selected protocol add DNS, Kerberos-Sec(TCP), Kerberos-Sec (UDP),Kerberos-Admin (UDP), LDAP, LDAP (UDP), LDAP (Global catalog), Microsoft CIFS (TCP) ,Microsoft CIFS (UDP), NTP (UDP), PING, RPC (All Interface), Click next.
On the Access Rules Sources, Click Add, Select Computers, Click New, Type Netbios name of DC and Type IP, Click Ok. Select DC and Click Add. Repeat this process for Front-End TMG server i.e. add name and IP of front-end TMG server and Click Add.
On the Access Rule Destinations, Click Add, from the computers list add DC and front-End TMG servers. Click Next and Click Finish. Apply changes and click ok.
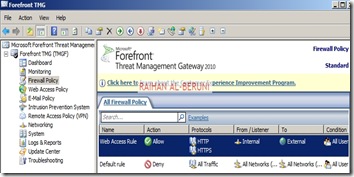
Create an Access Rule allowing all outbound traffic to go from internal to perimeter.
| Actions | Allow |
| Protocols | All Outbound Traffic |
| Source | Internal |
| Destination | Perimeter |
| Conditions | All Users |
Create another access rule allowing HTTP and HTTPS to go from internal to perimeter and external.
| Actions | Allow |
| Protocols | HTTP, HTTPS |
| Source | Internal |
| Destination | External |
| Conditions | All Users |
Configure Front-End Forefront TMG Server:
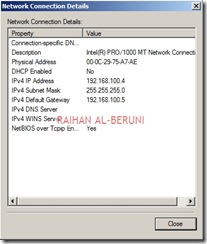
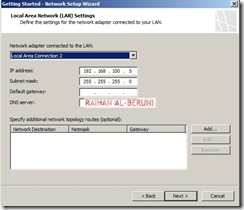
Prepare another Windows Server 2008 x64 computer. Log on as an administrator. Define internal and external IP addresses as shown below.
Internal TCP/IP property:
External TCP/IP property
Open Command prompt>type following command to add persistent Routing:
c:>Route Add –P DestinationIP DestinationMask SourceIP
c:>Route Print
Add Front-End TMG as domain member. Follow same installation and initial
configuration options shown in back-end TMG server. There are only two differences while initial Network Settings configuration that are selecting internal (192.168.100.0/24) and external (203.17.x.x/24) network. Those are shown below.
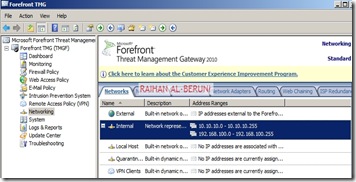
Create Connectivity Verifier with AD, DNS and Web.
Networking>networks>internal>Add 10.10.10.0/24 and 192.168.100.0/24 as internal IP. Make sure internal IP and perimeter IP of back-end server are both internal IP of Front-end server. keep default routing rules in Front-End TMG. Configure property of internal network.
Verify Network Rules:
Configure firewall to allow HTTP/HTTPS : Firewall Policy>New>Access policy>Allow HTTP and HTTPS for all users. Do not Allow all outbound traffic to go from internal to external in Front-End Server. Only specific ports and protocols should be allowed.
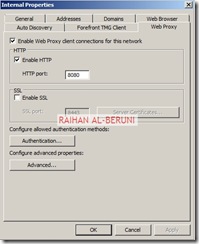
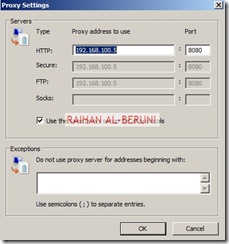
Test Firewall: Log on to a computer in internal network behind Back-End Firewall. Setup Proxy in IE as shown below and browse internet.
Placing Front-End Server(s) or a member server in DMZ:
One you have completed above steps, you are ready to place any Front-End server(s) such as Exchange CAS, OCS 2007 and SharePoint Servers in DMZ/Perimeter. You need to import certificates from Enterprise Root CA placed in internal network (behind Back-End TMG) to Front-End TMG server to publish secure web sites such as OWA, Outlook Anywhere or OCS. All Publishing Rules Applied in Front-End TMG server. Here, I am not writing OWA or Anywhere because it would redundant for me to write again as I have shown all these in my previous posting. Visit the links mentioned below.
Prerequisite for placing a member server in DMZ: A member server must have following TCP/IP configuration to work in perimeter.
| IP | 192.168.100.0/24 (Perimeter IP Range) |
| DG | 192.168.100.5 (Internal IP of Front-END TMG server) |
| DNS | 10.10.10.5 (Internal DNS) |
| 2nd DNS | 203.17.x.x (Public DNS) |
| Routing | As Mentioned in Persistent Routing Section of this Blog |